Top 25 Cybersecurity Frameworks To Consider
Содержание
During this stage, it was key to consider where you are in protecting your critical data from both organized cyber criminals and the insider threat. While a cybercriminal may be looking to sell your customer data to the highest bidder, an unhappy employee may be open to exploiting their access to digital information. These are core to a great cybersecurity program and a true professional can help create them. When it comes to troubleshooting complex security issues, diving deep, and analyzing anomalies – it’s really difficult to approach it prescriptively. SAML is a standard that defines a framework for exchanging security information between online business partners.
- Organizations can apply it to human and machine entities, partner companies, or other enterprise applications.
- Many different security activities and disciplines can benefit from standardized expression and reporting.
- Data protection is also key to the industry and is being forced by the European General Data Protection Regulation .
- View a detailed mapping of the relationship between the CIS Understanding Prescriptive Security Controls and ISO below.
- This security framework publication presents a new conceptual framework for providing information technology security training.
- A validated assessment is conducted by a HITRUST Authorized External Assessor, like BARR, and is the only assessment that produces a validated certification report.
Ensuring the security of these products and services is of the utmost importance for the success of the organization. This publication introduces the information security principles that organizations may leverage to understand the information security needs of their respective systems. The General Data Protection Regulation is the toughest privacy and security framework in the world. Though it was drafted and passed by the European Union , it imposes obligations onto organizations anywhere, so long as they target or collect data related to people in the EU.
The Hybrid Society: A Seamless Blend Of Physical And Online Public Services
The International Organization for Standardization provides independent, globally-recognized standards for securing technologies. ISO/IEC helps organizations defend against cyber threats and information security risks. View a detailed mapping of the relationship between the CIS Understanding Prescriptive Security Controls and ISO below. For example, you can use prescriptive analytics to determine the best social media engagement opportunities to take. The company Lithium Reach helps companies accomplish this by recommending the best time of day to post content via social media channels.
Hundreds of thousands of assets potentially targeted by hundreds of attack vectors can mean that your attack surface is made up of tens of millions to hundreds of billions of data points that must be monitored at all times. It is not enough to simply be able to list your inventory, fix your vulnerabilities and review your controls from time to time. You will need to automate security posture management in order to stay ahead of the adversary. Lastly, if you want to take this a step further once you know your unique risks, and you know your current security position relative to an accepted cybersecurity framework, you can have your cybersecurity team perform a skills assessment.
Essentially they predict multiple futures and allow companies to assess a number of possible outcomes based upon their actions. Prescriptive analytics use a combination of techniques and tools such as business rules, algorithms, machine learning and computational modelling procedures. These techniques are applied against input from many different data sets including historical and transactional data, real-time data feeds, and big data. PCI DSS directly applies to the protection of payment card data; think VISA, MasterCard, American Express, and Discover.
Understanding the similarities and differences across the top 25 security frameworks can help you create a more robust cybersecurity compliance program. In February 2014, through a series of workshops held throughout the country and with industry input, NIST released the “Framework for Improving Critical Infrastructure Cybersecurity” (“the Framework”). For the first time, the Framework provides industry with a risk-based approach for developing and improving cybersecurity programs. Its common sense, “English language” approach allows an organization and its directors to both identify and improve upon its current cybersecurity procedures. Though the Framework was developed for the 16 critical infrastructure sectors, it is applicable to all companies—albeit at least today—on a voluntary basis.
Inside Atos Ai Lab Making Ai Real For Business
Effective, cloud-based prescriptive data tools can help businesses achieve this benefit even quicker. Prescriptive analytics are relatively complex to administer, and most companies are not yet using them in their daily course of business. When implemented correctly, they can have a large impact on how businesses make decisions, and on the company’s bottom line.

Business must encrypt any personal information stored on a device (computer, phone, magnetic tape, flash drive, etc.) moved beyond the logical or physical controls of the data collector or data storage contractor. Subpart D establishes a framework to enable HHS to monitor and ensure compliance with the confidentiality provisions, a process for imposing a civil money penalty for breach of the confidentiality provisions, and hearing procedures. Imagine if businesses currently using on-premises system data as the basis for their predictive and prescriptive analytics could harness the power of the cloud?
Full BioPete Rathburn is a freelance writer, copy editor, and fact-checker with expertise in economics and personal finance. He has spent over 25 years in the field of secondary education, having taught, among other things, the necessity of financial literacy and personal finance to young people as they embark on a life of independence. It is important to not just be able to enumerate your controls, but also have an understanding of the effectiveness of each control in reducing your cyber risk. You can then make use of learning technologies to build a picture of how behaviors are changing over time.
Simplifying Hitrust Compliance Solutions
Banks and insurance companies need to adapt their security strategies in response; they need to detect and neutralize cyberattacks proactively before these reach their goal. To do this, banks and insurance companies must detect weak signals in near real time, which isn’t easy. Asher Security is a local Minnesota cybersecurity advisory and consulting business with the goal of helping businesses lower their risk by increasing their cybersecurity maturity. Understanding Prescriptive Security If you’d like to learn more about how we can help you please call us directly or fill out our contact form. But asking good questions and getting to the source of the problem requires tapping into our education and training, unique experiences, and skill sets. A great cybersecurity professional will start along a path and have the ability to dynamically adapt questions to eliminate issues and get closer to troubleshooting the ultimate issue.

We tend to procrastinate or ignore the unknown and the things that are difficult. In cybersecurity that might mean that an old technology we never learned about, have no qualified security tools for, and can’t retire goes unattended within the company network. I’m not saying everyone does this, I’m just being honest and saying as humans we https://globalcloudteam.com/ have this tendency. I think the real driver behind prescript security is a leadership desire to feel more confident the right security controls are being applied to the proper risks. I’m all about process and systems, and continuous improvement, but most often times prescriptive security completely solve the issue it was intended to solve.
ISO sets standards for various technologies, including several security standards. The ISO/IEC “family” boasts over a dozen standards, but ISO sets the foundation for establishing an information security management system . The HITRUST CSF (created to stand for “Common Security Framework”, since rebranded as simply the HITRUST CSF) is a prescriptive security framework that meets the requirements of multiple regulations and standards. The framework provides a way to comply with standards such as ISO/IEC series and HIPAA. This proactive approach to security uses big data analytics and automation to detect security events more precisely.
Program On Corporate Governance Advisory Board
Implementation Group 3 is for mature organizations with significant resources and cybersecurity expertise. This security framework guidance is designed to help organisations protect themselves in cyberspace. It breaks down the task of defending your networks, systems and information into its essential components, providing advice on how to achieve the best possible security in each of these areas.

To ensure cybersecurity risks are properly managed throughout the Member Organizations. To achieve an appropriate maturity level of cybersecurity controls within the Member Organizations. New Zealand’s PSR creates a policy framework for how organizations should manage security governance , personnel , information , and physical security across the public and private sectors. It focuses on the outcomes that are required to achieve a proportionate and risk-managed approach to security that enables government business to function effectively, safely and securely. Organizations rely heavily on the use of information technology products and services to run their day-to-day activities.
Google Cloud Next 2022
CIS-CAT Pro, our automated configuration assessment tool, has been validated by the NIST Security Content Automation Protocol to audit systems subject to FISMA requirements in the FDCC Scanner and Authenticated Configuration Scanner. Become a CIS member, partner, or volunteer—and explore our career opportunities. To noon CST for an open Q&A and discussion of the process and benefits of obtaining a HITRUST Certification.
Each information security framework was created for a purpose, but the shared goal is some form of assurance that sensitive data is effectively protected. Unfortunately, compliance requests vary by client and too frequently are based on incorrect assumptions or a check-list mentality that jeopardizes true information security. Organizations typically have limited resources and familiarity with the Framework to help them leverage their existing cybersecurity, compliance and audit programs, policies and processes. HITRUST also offers a risk assessment tool called MyCSF to help in the implementation of the framework. MyCSF is a secure, web-based solution for performing assessments, managing remediation activities, and reporting and tracking compliance.
Hitrust Resources
Organizations can leverage these standards to determine the appropriate level of security protections required, ensuring efficient utilization of security budgets. Many critical infrastructure organizations are required to meet multiple regulations with overlapping and conflicting requirements. In order to avoid fines and additional fees from regulatory bodies, many operators are forced to maintain multiple compliance documents describing how the organization is complying with each requirement. The standard developed by the Framework enables auditors to evaluate cybersecurity programs and controls in one standard format eliminating the need for multiple security compliance documents. SecurityScorecard’s security ratings platform and Atlas offering enable organizations to monitor their cybersecurity and compliance posture more efficiently. Our security ratings provide real-time visibility into cybersecurity risks, using an easy-to-read A-F scoring system.
Getting Started With Prescriptive Analytics
It analyzes raw data about past trends and performance through machine learning to determine possible courses of action or new strategies generally for the near term. In response, financial market regulators are responding to cyber threats by taking a more prescriptive approach to cybersecurity. By and large, existing cybersecurity regulation of capital markets and banking intermediaries has been principles- and standards-based, in the form of examination guidance, rather than prescriptive, rules-based regulation.
Tom Wheeler, Chairman of the Federal Communications Council , stated that an industry-driven cybersecurity model is preferred over prescriptive regulatory approaches from the federal government. Nonetheless, it continues to see successful attacks on critical infrastructure organizations. The HITRUST CSF was developed to address the multitude of security, privacy, and regulatory challenges facing organizations. This directory includes laws, regulations and industry guidelines with significant security and privacy impact and requirements.
This result in an accurate picture of where your cyber-risk is and helps you prioritize risk mitigation actions while avoiding busy work fixing low risk issues. Any device, application, service, or cloud instance that has access to your enterprise network or data. Enterprise attack surfaceFor a medium to large sized enterprise, the attack surface can be gigantic.
Larger companies are successfully using prescriptive analytics to optimize production, scheduling and inventory in the supply chain to make sure they are delivering the right products at the right time and optimizing the customer experience. Though “voluntary,” it cannot be overstated that the Framework is “a National Standard” developed with input from industry experts, collaborators and businesses with years of cyber experience. As stated by the Chairman of the House of Intelligence, Mike Rogers, “there are two kinds of companies.
Notas del día:
Jun 16, 2025 / 14:47
Veracruz le desea éxito a Claudia Sheinbaum en el G7: Rocío Nahle
Jun 16, 2025 / 14:42
Veinte sentadillas y no pagas boleto del camión, así combaten el sedentarismo en Rumania
Jun 16, 2025 / 14:26
Impugnan elección en Coahuitlán
Jun 16, 2025 / 14:09
Salsa Fest dejó más de 837 mdp en Veracruz y casi 600 mil asistentes
Jun 16, 2025 / 13:57
Impulsará Congreso preservación de lenguas originarias de Veracruz
Jun 16, 2025 / 13:51
Será gratis el reemplacamiento de motos para quienes estén al corriente: Gobernadora 📹
Jun 16, 2025 / 13:42
Igor Rojí será el nuevo secretario de Turismo en Veracruz
Jun 16, 2025 / 13:25
Se desploman 70% las ventas por pavimentación del centro histórico: Restauranteros 📹
Jun 16, 2025 / 13:16
Jun 16, 2025 / 13:16
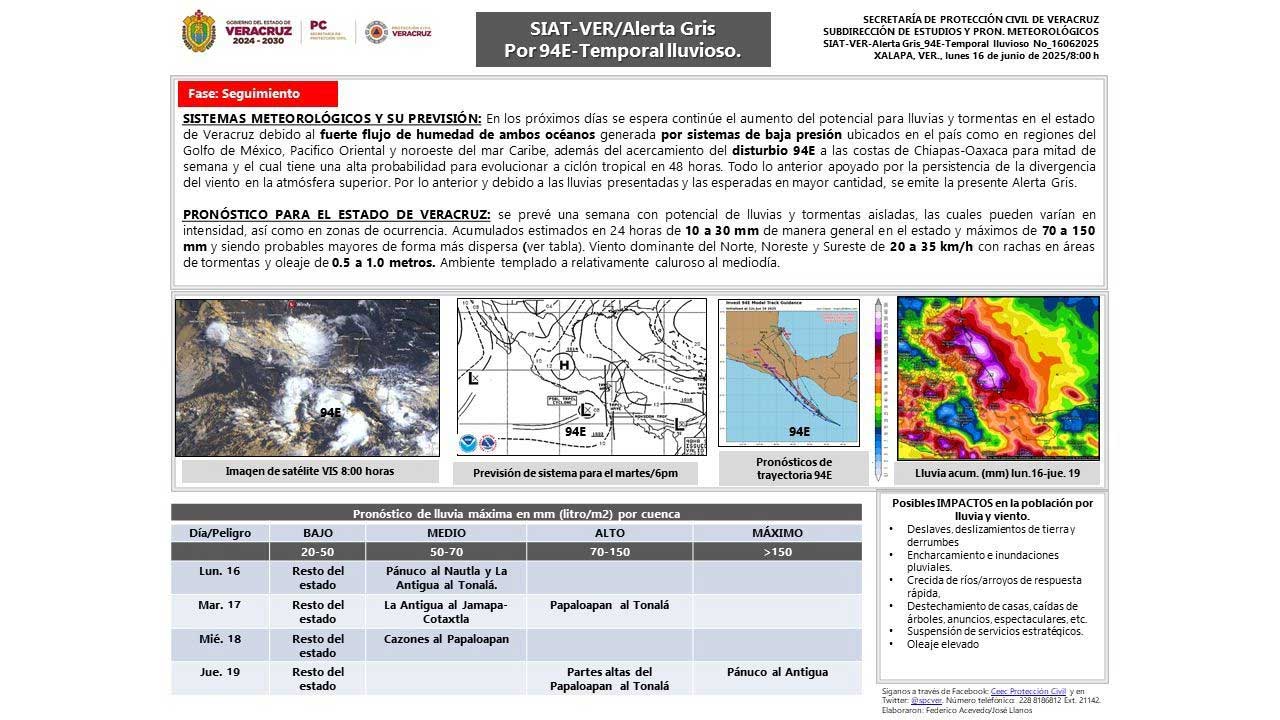
Emiten Alerta Gris por disturbio tropical 94E en Veracruz 📹
Jun 16, 2025 / 13:09
Jun 16, 2025 / 13:04
Comunidad LGBTTTIQ+ confía en que se les abran más espacios laborales 📹